Reverse engineering a router - Part 1
- Part 1: Enumerating Components and Finding Serial Ports
Some time ago I decided to learn how to attack, gain privilege access and perform modifications to hardware such as routers or IoT devices. In these collection of posts, I will be doing a walkthrough on how to reverse engineer a router, in specific the following one:

Enumerating Components and Finding Serial Ports
The first we are going to do is analyzing the PCB and gather information about the components and find if there is any visible debug port. Debug ports were designed by the engineers and left in the PCB for debugging the systems and physical connections between the pins.
Looking at the board we can see the following components and debug ports:

Main IC:
SoC:
- Broadcom BCM6328
- BMIPS4350 @ 320 MHz
- BMIPS4350 @ 320 MHz
Datasheet: BCM6328
2nd IC:
- BCM43225 802.11b/g/n (2x2)
- MAC/Baseband
- RF Transceiver
RAM:
- ProMOS V59C1512164QDJ25
- SDRAM DDR2-800
- 64MB
Datasheet: V59C1512164QDJ25
FLASH:
- MX25L128
Datasheet: MX25L128
UART:

Maybe you are wondering how I got the UART pinout. The best way to do this, is using a multimeter and checking the voltage behavior in the pins just after the router is switched on:
- Vcc: 3.3 V
- Tx: Is pulled high (same as Vcc) and dropped 2-1 V when sending data
- Rx: Is pulled high (same as Vcc)
In case you still don’t know which is Tx and which one is Rx, you can use a logic analyzer and sniff the serial communication. I am using this simple logic analyzer:

And it looks like this after attaching it to the UART:

And Logic program from Saleae.
In the program, you will need configure the baudrate so it can decode the serial communication. I used baudrate tool from devttys0 to get the baudrate, but you can get this value by seeing the symbols and the Tx time of them to get this value.

Now that we have everything ready, lets start sniffing communication in the UART:
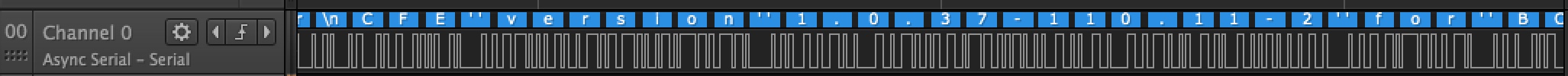
The logic analyzer was able to decode some data from the UART, and we can see clearly: CFE version 1.0.37-110.11-2 for BCM96328 (32bit,SP,BE).
Getting shell via UART
We will be using a FT232H, which is a chip from FTDI that works like an USB to serial converter but includes many serial protocols such as UART, SPI, I2C, JTAG, SWD…
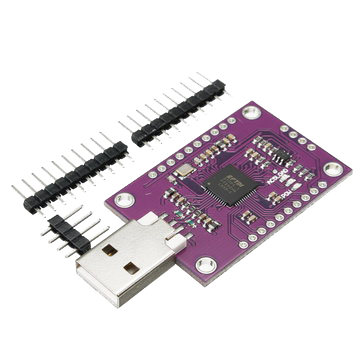
Datasheet: FT232H
From the datasheet, we know ADBUS0 or AD0 (Tx) and ADBUS1 or AD1 (Rx) are the pins for the Async serial communication.
We connect the Tx pin from router to the Rx pin in the FT232H and the Rx from the router to the Tx from the FT232H. Now its time to connect to port:
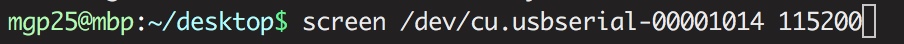
And switch the router on!
We haven"t accessed shell yet, but we can see relevant information:
|
|
PreSharedKey matches with router sticker:

The router is using Busybox:
BusyBox v1.00 (2011.09.13-03:40+0000) Built-in shell (msh)
and squashfs filesystem.
Wait a minute or so until the system has boot up and type help or whatever:
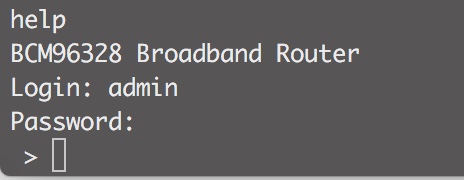
Unfortunately, the commands are limited but we can still obtain some credentials:

You can use tools like JohnTheRipper to crack these passwords:
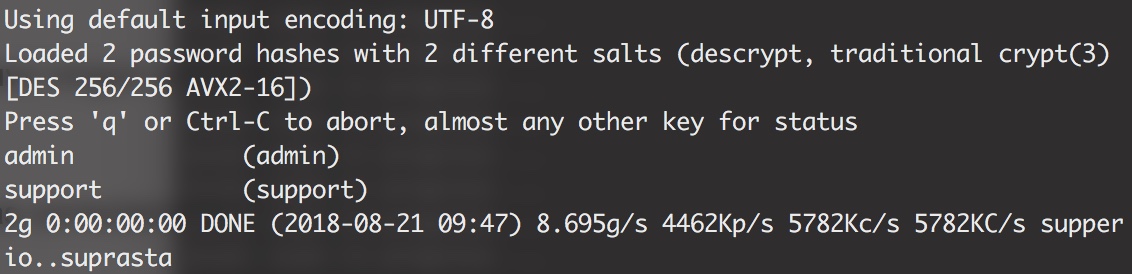
It was obvious:
|
|
We still haven’t access to shell. We will try doing command injection to get it:

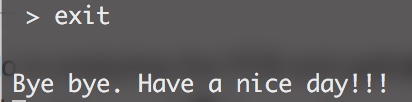
So far, cat | sh worked! We are in!
Hope you have enjoyed this brief post.